
The scenario is usually the following: if it’s a public online service attackers will usually make every effort to create exact copies of a real message. However, if attackers are hunting for access to an internal system, they often have to use their imagination as they might not know how the email should appear.
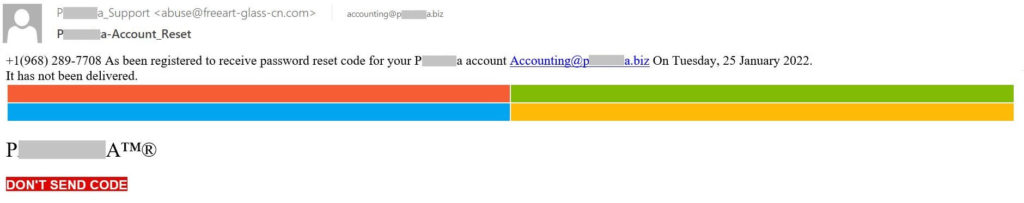
Everything about this message looks ridiculous, from the incorrect language to the rather dubious logic — it seems to be at once about linking a new phone number and about sending a password reset code. Nor does the “support” e-mail address lend credibility to the message: there is no plausible reason why a support mailbox should be located on a foreign domain (let alone a Chinese one).
The attackers are hoping that their victim, fearing for the security of their account, will click the red DON’T SEND CODE button. Once done, they’re redirected to a website mimicking the account login page, which, as you’d imagine, just steals their password. The hijacked mail account can then be used for BEC-type attacks or as a source of information for further attacks using social engineering.
“Spam and phishing attacks are probably the most underappreciated type of cyberthreats. Even the most responsible employees can be tricked into clicking on them, everyone tends to lose their focus in the hustle of a working day. Good news is modern cybersecurity solutions are often equipped with proper despams filters, and most employees’ trainings in cybersecurity hygiene are successful at preventing such incidents from occurring,” says Maria Garnaeva, cybersecurity expert at Kaspersky.
What to explain to company employees
To minimise the chances of cybercriminals getting their hands on employees’ credentials, communicate the following to them:
Comments
Post a Comment